Actions
Bug #25090
closedMissing reports with firewall technique
Added by Nicolas CHARLES about 1 year ago. Updated about 1 year ago.
Pull Request:
Severity:
UX impact:
User visibility:
Effort required:
Priority:
0
Name check:
To do
Fix check:
Checked
Regression:
No
Description
Service Start does not report, and if no configuration is given, then it has also no "Load configuration" report
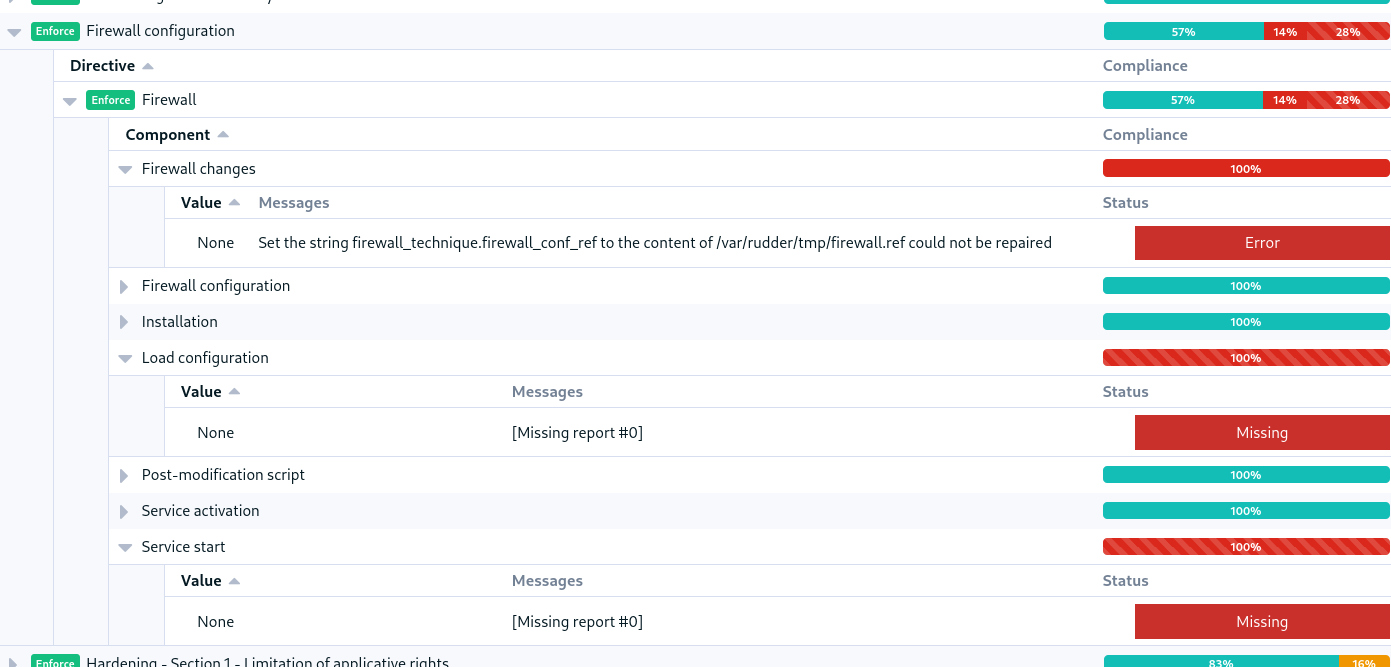
Files
| clipboard-202407011139-wcmle.png (83.7 KB) clipboard-202407011139-wcmle.png | Nicolas CHARLES, 2024-07-01 11:39 |
 Updated by Nicolas CHARLES about 1 year ago
Updated by Nicolas CHARLES about 1 year ago
reports are
2024-07-01T09:36:07+00:00 rudder info: Successfully installed package 'nftables'
E| repaired firewall Installation Presence of package nftables in any version was repaired
2024-07-01T09:36:07+00:00 rudder info: Inserted the promised line 'flush ruleset' into '/etc/nftables.conf' after locator
2024-07-01T09:36:07+00:00 rudder info: Inserted the promised line '' into '/etc/nftables.conf' after locator
2024-07-01T09:36:07+00:00 rudder info: insert_lines promise 'flush ruleset
2024-07-01T09:36:07+00:00 ' repaired
2024-07-01T09:36:07+00:00 rudder info: Moved '/etc/nftables.conf_1719826563_Mon_Jul__1_11_36_07_2024.cf-before-edit' to repository location '/var/rudder/modified-files/_etc_nftables_conf_1719826563_Mon_Jul__1_11_36_07_2024_cf_before_edit'
2024-07-01T09:36:07+00:00 rudder info: Edited file '/etc/nftables.conf'
E| repaired firewall Firewall configuration Build file /etc/nftables.conf from string template was repaired
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
E| error firewall Firewall changes Set the string firewall_technique.firewall_conf_ref to the content of /var/rudder/tmp/firewall.ref could not be repaired
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
2024-07-01T09:36:07+00:00 error: CfReadFile: Could not examine file '/var/rudder/tmp/firewall.ref' (stat: No such file or directory)
info firewall Firewall changes Set the string firewall_technique.firewall_conf to the output of 'nft --stateless list ruleset' was correct
2024-07-01T09:36:07+00:00 R: The 'nft --stateless list ruleset' command returned ''
info firewall Firewall changes Create the condition rudder_firewall_conf_repaired_{true,false} with true was correct
2024-07-01T09:36:07+00:00 R: Condition rudder_firewall_conf_repaired_true defined
info firewall Firewall changes Create the condition rudder_firewall_reload_{true,false} with rudder_firewall_conf_repaired_true|rudder_firewall_technique_conf_false was correct
2024-07-01T09:36:07+00:00 R: Condition rudder_firewall_reload_true defined
2024-07-01T09:36:07+00:00 R: [INFO] Executing is-enabled on nftables using the systemctl method
2024-07-01T09:36:07+00:00 rudder info: Executing 'no timeout' ... '/bin/systemctl --no-ask-password enable nftables'
2024-07-01T09:36:07+00:00 rudder info: Completed execution of '/bin/systemctl --no-ask-password enable nftables'
2024-07-01T09:36:07+00:00 R: [INFO] Executing enable on nftables using the systemctl method
E| repaired firewall Service activation Ensure service nftables is enabled at boot was repaired
2024-07-01T09:36:07+00:00 R: [INFO] Executing is-active on nftables using the systemctl method
2024-07-01T09:36:07+00:00 rudder info: Executing 'no timeout' ... '/bin/systemctl --no-ask-password reset-failed nftables'
2024-07-01T09:36:07+00:00 rudder info: Completed execution of '/bin/systemctl --no-ask-password reset-failed nftables'
2024-07-01T09:36:07+00:00 rudder info: Executing 'no timeout' ... '/bin/systemctl --no-ask-password start nftables'
2024-07-01T09:36:07+00:00 rudder info: Completed execution of '/bin/systemctl --no-ask-password start nftables'
2024-07-01T09:36:07+00:00 R: [INFO] Executing start on nftables using the systemctl method
info firewall Service start Ensure that service nftables is running could not be repaired
2024-07-01T09:36:07+00:00 rudder info: Executing 'no timeout' ... '/bin/systemctl --no-ask-password reload nftables'
2024-07-01T09:36:07+00:00 rudder info: Completed execution of '/bin/systemctl --no-ask-password reload nftables'
2024-07-01T09:36:07+00:00 R: [INFO] Executing reload on nftables using the systemctl method
info firewall Load configuration Reload service nftables could not be repaired
info firewall Load configuration Set the string firewall_technique.current_config_new to the output of 'nft --stateless list ruleset' was correct
2024-07-01T09:36:07+00:00 rudder info: Created file '/var/rudder/tmp/firewall.ref', mode 0600
2024-07-01T09:36:07+00:00 rudder info: Inserted the promised line '' into '/var/rudder/tmp/firewall.ref' after locator
2024-07-01T09:36:07+00:00 rudder info: insert_lines promise '' repaired
2024-07-01T09:36:07+00:00 rudder info: Moved '/var/rudder/tmp/firewall.ref_1719826563_Mon_Jul__1_11_36_07_2024.cf-before-edit' to repository location '/var/rudder/modified-files/_var_rudder_tmp_firewall_ref_1719826563_Mon_Jul__1_11_36_07_2024_cf_before_edit'
2024-07-01T09:36:07+00:00 rudder info: Edited file '/var/rudder/tmp/firewall.ref'
info firewall Load configuration Insert content into /var/rudder/tmp/firewall.ref was repaired
E| n/a firewall Post-modification script Post-hook command was not applicable
 Updated by Nicolas CHARLES about 1 year ago
Updated by Nicolas CHARLES about 1 year ago
- Status changed from New to In progress
- Assignee set to Nicolas CHARLES
 Updated by Nicolas CHARLES about 1 year ago
Updated by Nicolas CHARLES about 1 year ago
- Status changed from In progress to Pending technical review
- Assignee changed from Nicolas CHARLES to Félix DALLIDET
- Pull Request set to https://github.com/Normation/rudder-techniques/pull/1847
 Updated by Nicolas CHARLES about 1 year ago
Updated by Nicolas CHARLES about 1 year ago
- Status changed from Pending technical review to Pending release
Applied in changeset rudder-techniques|9552c7d487d6c10097f9827f1c8f837293fad0e8.
 Updated by Alexis Mousset about 1 year ago
Updated by Alexis Mousset about 1 year ago
- Fix check changed from To do to Checked
 Updated by Vincent MEMBRÉ about 1 year ago
Updated by Vincent MEMBRÉ about 1 year ago
- Status changed from Pending release to Released
This bug has been fixed in Rudder 8.1.6 which was released today.
Actions